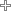Course Outcomes
|
6CS4-03.1 |
Identify services that enhance the security and its mechanism. |
|
6CS4-03.2 |
Classify security attacks on information over network. Describe and apply classical encryption techniques. |
|
6CS4-03.3 |
Explain and apply modern block cipher with modes |
|
6CS4-03.4 |
Compare conventional encryption algorithms & public key cryptography, and design Encryption algorithm to provide the Integration and confidentiality of a message. |
|
6CS4-03.5 |
Understand the concept of hash function with application and message authentication code in security system |
|
6CS4-03.6 |
Classify key management schemes and discuss web security and transport level security protocols. |
Mapping of COs and POs
|
CO |
PO1 |
PO2 |
PO3 |
PO4 |
PO5 |
PO6 |
PO7 |
PO8 |
PO9 |
PO10 |
PO11 |
PO12 |
PSO 1 |
PSO 2 |
PSO 3 |
|
CO1 |
2 |
- |
2 |
- |
- |
- |
- |
2 |
- |
- |
- |
2 |
2 |
- |
2 |
|
CO2 |
2 |
2 |
3 |
2 |
- |
- |
- |
- |
- |
- |
- |
2 |
2 |
- |
- |
|
CO3 |
3 |
2 |
- |
- |
- |
- |
- |
- |
- |
- |
- |
2 |
3 |
- |
2 |
|
CO4 |
2 |
1 |
2 |
- |
- |
- |
- |
- |
- |
- |
- |
- |
3 |
- |
2 |
|
CO5 |
2 |
2 |
1 |
- |
- |
- |
- |
- |
- |
- |
- |
2 |
3 |
- |
2 |
|
CO6 |
2 |
2 |
3 |
2 |
- |
- |
- |
- |
- |
- |
- |
2 |
2 |
- |
2 |
|
Avg |
2.2 |
1.8 |
2.2 |
2 |
- |
- |
- |
2 |
- |
- |
- |
2 |
2.5 |
- |
2 |